A honey pot is a computer system on the Internet that is expressly set up to attract and “trap” people who attempt to penetrate other people’s computer systems. Generally, a honeypot consists of data (for example, in a network site) that appears to be a legitimate part of the site but is actually isolated and monitored, and that seems to contain information or a resource of value to attackers, which are then blocked. This is similar to the police baiting a criminal and then conducting undercover surveillance, and finally punishing the criminal.
A honeypot works by fooling attackers into believing it is a legitimate system; they attack the system without knowing that they are being observed covertly. When an attacker attempts to compromise a honeypot, attack-related information, such as the IP address of the attacker, will be collected. This activity done by the attacker provides valuable information and analysis on attacking techniques, allowing system administrators to “trace back” to the source of attack if required.
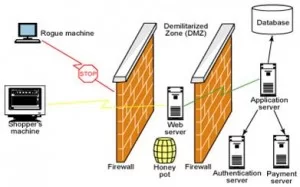
Honeypots can be classified based on their deployment and based on their level of involvement.
Classification based on Deployment
1) Production Honeypot: A production honeypot is used for risk mitigation. Most production honeypots are emulations of specific operating systems or services. They help to protect a network and systems against attacks generated by automated tools used to randomly look for and take over vulnerable systems. By running a production honeypot, the scanning process from these attack tools can be slowed right down, thereby wasting their time. Some production honeypots can even shut down attacks altogether by, for example, sending the attackers an acknowledgement packet with a window size of zero. This puts the attack into a “wait” status in which it could only send data when the window size increases. In this way, production honeypots are often used as reconnaissance or deterrence tools.
2) Research Honeypots: Research honeypots are real operating systems and services that attackers can interact with, and therefore involve higher risk. They collect extensive information and intelligence on new attack techniques and methods, and hence provide a more accurate picture of the types of attacks being perpetrated. They also provide improved attack prevention, detection and reaction information, drawn from the log files and other information captured in the process. In general, honeypot research institutions such as universities and military departments will run research honeypots to gather intelligence on new attack methods. Some of the research results are published for the benefit of the whole community.
Classification based on Interaction
1) Low-interaction: One or more simple services are made available which log all communication attempts to specific services, like a web or SSH server. Usually these are just simple daemons which provide the person who configured them a passive way to monitor attack attempts. The host operating system is not vulnerable to attacks, so low interaction honey- pots are fairly safe to run, but are also unable to be used where a more complex, interactive environment is needed, like a SMTP server.
2) Medium-interaction: Medium level honeypots begin to emulate collections of software to present a more convincing front to the attacker, but still shield the host operating system. Emulating a collection of software can become quite complex, since the emulated programs should respond the same way as their real counterparts, but must not have the same security issues, otherwise the emulation will break. Further, there are more points of attack for the malicious user, so the chance of system compromise is raised.
3) High-interaction: Finally there are high-interaction honeypots. The full host operating system is presented to the attacker, along with actual instances of programs, instead of their emulations. The usual goal of high-interaction honeypots is for the attacker to gain root access on the machine, and then see what he does. Because of this goal, this level of honeypot has the highest risk, but also the highest potential for collecting information. Honeypots at this level need constant supervision, since the attacker will actually control it, and could try to use it as a jumping-off point for further attacks.
By luring a hacker into a system, a honeypot serves several purposes:
•The administrator can watch the hacker exploit the vulnerabilities of the system, thereby learning where the system has weaknesses that need to be redesigned.
•The hacker can be caught and stopped while trying to obtain root access to the system.
•By studying the activities of hackers, designers can better create more secure systems that are potentially invulnerable to future hackers.
It is important to remember that Honey Pots do not replace other traditional Internet security systems; they are an additional level or system. Maintaining a honey pot is said to require a considerable amount of attention and may offer as its highest value nothing more than a learning experience.

